BackupChain Backup Software Concepts
For detailed product information, please visit the BackupChain home page.
If you handle and store important data on your computers, it is important for you to be aware of the following concepts related to data backup.
Sector-Level Disk Backup vs. File Backup vs. Virtual Machine Backup
Sector-level disk backup is a process where the entire disk is being copied to another disk or a virtual disk, or a container file. Disk backup doesn’t have to be aware of what’s in the disk; disk backup is a sector-by-sector copy of a disk and includes whatever may be stored on disk, including hidden areas, encrypted files, file fragmentation, etc.
File backup is a process where the backup application processes each file or document separately. File backup offers many benefits over disk backup, such as file versioning, where the entire history of a document is available for restore. In addition, file backup can be tuned to quickly skip unchanged or unwanted files in the backup. BackupChain also offers a way to change how each type of file is processed (compression, encryption, deduplication, file history length, cleanup, etc.) depending on its file extension.
While disk backup is useful to take a backup of the Windows operating system in its entirety, it’s not recommended as a replacement of file backups. Similarly, file backups alone can’t restore the Windows operating system; hence, most IT administrators chose a hybrid backup strategy: A sector-level disk backup when the server or PC is fully installed with all applications and perhaps once or twice a year after that. File backups, on the other hand, are utilized to make sure all important documents are backed up as often as necessary to avoid losses. Since file backups skip quickly all unchanged portions of your file server structure, they can run several times a day without having an impact on your server’s quality of service and without consuming excessive backup storage.
Virtual machine backup is a specialized backup process where backups of virtual machines are taken from the host without interrupting or otherwise interfering with the virtual machines on the host. The virtual machine backup process talks to the virtualization platform (for example, Hyper-V) to bring the VM into a consistent state before backup. It then takes a consistent file backup of all relevant VM files, which are then compressed, encrypted, and or deduplicated.
Compression
Compression is a method by which the size of a file is reduced based on repetitive patterns within a file’s content. For example, if certain words repeat many times inside a Microsoft Word Document, the compression program replaces each word with a much shorter code.
Some types of files usually do not contain repetitive patterns. For example, WAV, AVI, MP3, and other media or music files are usually not compressible because their content is random and not repetitive.
On the other hand, text files, program files, databases, and virtual machine image files, usually contain a good portion of blank space and repeated blocks; hence, it is recommended to compress such files.
BackupChain Backup Software is shipped with various presets so that it turns compression on and off automatically depending on the type of a file; however, you change the configuration and determine yourself whether you want to compress a given file type or not.
Encryption
Encryption is a method that “randomizes” data to a point where it cannot be recognized. Symmetric cyphers are programs that use the same password and method to encrypt and decrypt information. If you decide to encrypt your files, BackupChain will use an AES256 symmetric cypher to encrypt your files. AES is an open international industry standard for data security and is considered one of the most secure and efficient algorithms for encryption (see http://en.wikipedia.org/wiki/Advanced_Encryption_Standard for more information.)AES256 is also HIPAA compliant.
Without a password it is usually impossible to recover an encrypted file. Therefore if you forget your password there is no way to restore your backup files.
Deduplication (Delta Compression)
Deduplication, also known as Delta Compression, is a method that compares a file to its previous contents. For example, if an incremental daily file backup is generated, BackupChain compares yesterday’s copy with today’s file contents to find the actual differences. Then, a delta file is generated that contains only the changes.
Differential deltas compare the changes that occurred between now and the first backup that was taken (also called “full delta” or “full copy”).
Because delta files (the detected file content changes between backup cycles) may contain repetitive patterns, it makes sense to compress them as well. BackupChain is configured to compress delta files automatically to save even more space in your backup folder or device.
Backup Tasks
A backup task is a group of items you wish to back up in one process. For example, you can configure BackupChain to back up your My Documents folder and your virtual machines at the same time.
Backup Tasks may be scheduled to run at predetermined times, such as every 30 minutes, every night at 10 PM, or weekly on Saturdays.
With BackupChain you can set up as many tasks as you need and run them simultaneously if necessary.
Scheduler: The Auto-Pilot
A scheduler is a background process that starts backup tasks automatically when the trigger event occurs. BackupChain runs a scheduler as a Windows Service in the background; hence, you do not need to be logged on to Windows for backup tasks to start. As long as the computer is switched on, backups will start at the configured time intervals.
BackupChain’s scheduler supports several types of schedules:
Continuous: Run a task at given intervals. For example, every X minutes, hours, days, or weeks. The task will be repeated indefinitely at specified intervals.
Daily: Run tasks every n days at a particular start time. For example, at 8 AM every third day, or 11PM every night.
Weekly: Run tasks on specific days every nth week. For example, you can set up a task to run on Mondays, Wednesdays, and Sundays at 9PM every second week.
Monthly: Run tasks on specific months, days of the month, and weeks of the month. Example #1: Run backups on every 2nd day of each month. Example #2: Run tasks every third Monday in January, March, and June.
Network Folders
A network folder (or network share) is a data folder located on another computer connected through a private local area network (LAN) or VPN (virtual private network).
There are two ways to access network shares and both require authentication. Authentication is the transmission of a user name and password to the other computer before the remote computer grants access to its files.
One way to access the network folder is using a UNC path. This is the method supported by BackupChain and it’s also the most flexible method. These are several examples of UNC paths and how they should be entered in BackupChain:
\\computername\foldername
\\computername.domainname\foldername
\\<ip address>\\folder as in: \\192.168.1.1\foldername
When connecting to a network folder it’s very important to let Windows know how to authenticate. The user name should be prefixed with the domain or server network name or address to make it clear how the authentication is to be made.
Examples for user names, instead of joe use: joesdomain\joe (in a domain setting)
OR
192.1.3.5\joe (in a workgroup or mixed setting to authenticate as user Joe created on server with address 192.1.3.5)
OR
Fileserver4\joe (in a workgroup or mixed setting to authenticate as user Joe created on server “fileserver4”)
Domains and Workgroups
A Windows Domain requires a Domain Controller, which is a computer that manages user accounts and their access permissions. Workstations and servers authenticate with domain controllers in order to obtain access to resources on the local network.
A workgroup is a decentralized network approach without a domain controller. In a workgroup, computers share resources when they belong to the same workgroup.
Windows User Accounts
Microsoft Windows uses a user session concept to protect your computer and network from unauthorized access and damage resulting from malicious software, such as viruses.
Users may have restricted rights. For example, the built-in SYSTEM user has access to almost everything, while a guest user account may not be allowed to access certain folders on the computer. Similarly, you can share a folder to others on the network and specify which users can read and who is permitted to write and delete inside that folder.
Most people are not aware of it but your computer runs several user sessions simultaneously. Each Windows PC has a SYSTEM user and several other users with restricted access to files and network resources. BackupChain’s background service, which actually runs the backups even when you are not logged on to Windows, runs in the session of the local system user.
Anti-virus programs and other services on your computer run in different user sessions, invisible to your personal user session. It is important to know that network connections are not visible to other user sessions. Mapped drives and network shares cannot be created and authenticated in one session and accessed by another. Hence, if you personally have access to a network folder, these access rights are private to your user session. Other user sessions, such as the local system user, do not have the same access permissions as you have. This was done that way for several reasons. First it protects your machine from virus damage and security breaches. Second, it allows several people to work simultaneously on one single computer (this is especially important for servers).
Authentication
When connecting to a network drive it is important to understand how authentication works.
In Microsoft Windows, each computer may have several user accounts of its own and several users may be logged in to the same computer simultaneously. For example, you may be logged in physically as user “Sven” and system processes in the background may be using internal user accounts to run applications, such as “SYSTEM”. In addition, Windows Servers permit multiple administrators to work via Remote Desktop on the same server simultaneously, each with their own account and desktop screens.
Problems may arise when several users connect to the same remote server or when several similar user names exist. This is why you should use the following pattern to connect to a network share:
\\servername.domainname\foldername
And then log in using this use name pattern:
Domainname\YourDomainUserName
If connecting to a computer that isn’t on a domain:
\\ RemoteServerName \FolderName
And use this user name pattern:
RemoteServerName\UserNameOn RemoteServer
This method ensures Microsoft Windows understands which user and which server you mean.
On a simple network without domains you can use a simpler login:
\\servername\folder
And log in with the user name.
Common Network Connection Challenges
BackupChain runs backups in a background service called “BackupChain Service” and it is using the local system user session. Note: Backups do not run in the application visible to the user. Because the background process uses the local system user, that user needs to authenticate separately with each network server used.
Your own user session may be connected to the network share but the local system user is a separate session which has its own set of network connections, different from yours. When you add a network share to BackupChain, it uses the login credentials you entered to authenticate with the other computer on the network.
Note: You cannot use two different users to connect to the same server on the network. Example: Say you have a server named dataserver and it contains two shares: datafiles and musicfiles. You can use Dataserver\user1 to connect to \\dataserver\datafiles and \\dataserver\musicfiles
You cannot connect two users to connect from one PC to one server:
Dataserver\user1 to connect to \\dataserver\datafiles
And Dataserver\user2 to connect to \\dataserver\musicfiles
Note: The above limitation is a Microsoft Windows limitation and applies across all user sessions on your computer. Hence you need to give the BackupChain the same user credentials that you use personally in your user session. You cannot connect two different users to the same remote server simultaneously.
An alternative is not to use the local system user for BackupChain’s background service. Open the Service Manager or Services from the Control Panel using the Windows Start menu. Look for the service called “BackupChain Service” and open its properties (see screenshot below). Navigate to the Log On tab and change the user from local system account to a local administrator or a domain administrator. If you are on a domain, that user needs to be a local admin and also have permissions on the remote server. If you want to change the user for BackupChain’s background service you have to select a local administrator user.
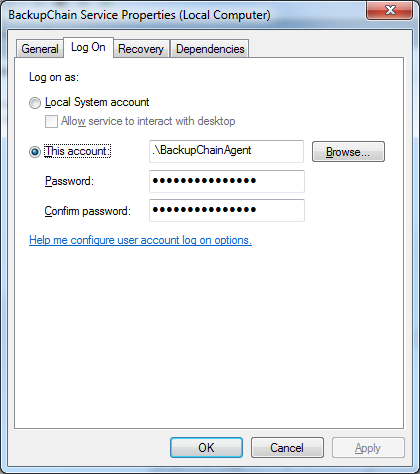
Network Drives Accessed via a Mapped Drive Letter
Do not use mapped drives in BackupChain. In fact, BackupChain will not show mapped drives in the folder and file selection screens. The reasons have been stated in the previous section.
Mapped drives are user session specific. BackupChain’s background service runs as local system user and does not have access to the mapped drives you use personally when you log in using your own user name.
Instead you need to provide a UNC path to the network share
with user name and password, see section above. You may also need to change the
Windows user for the BackupChain’s background service as described in the
previous section.
Backup Software Overview
The Best Backup Software in 2026 Download BackupChain®BackupChain Backup Software is the all-in-one Windows Server backup solution and includes:
Server Backup
Disk Image Backup
Drive Cloning and Disk Copy
VirtualBox Backup
VMware Backup
FTP Backup
Cloud Backup
File Server Backup
Virtual Machine Backup
Server Backup Solution
Hyper-V Backup
Popular
- Best Practices for Server Backups
- NAS Backup: Buffalo, Drobo, Synology
- How to use BackupChain for Cloud and Remote
- DriveMaker: Map FTP, SFTP, S3 Sites to a Drive Letter (Freeware)
Resources
- BackupChain
- VM Backup
- Knowledge Base
- BackupChain (German)
- German Help Pages
- BackupChain (Greek)
- BackupChain (Spanish)
- BackupChain (French)
- BackupChain (Dutch)
- BackupChain (Italian)
- BackupChain Server Backup Solution
- BackupChain is an all-in-one, reliable backup solution for Windows and Hyper-V that is more affordable than Veeam, Acronis, and Altaro.

